Technical feasibility is the quiet force that decides whether your project ships or stalls. In product management, a solid technical feasibility assessment tells you if the thing you want to build can, in fact, be built with your current stack, people, and constraints. Skip it, and costs rise while confidence falls.
# What technical feasibility really means
Technical feasibility is more than checking if a technology exists. It is a structured evaluation of capabilities, architecture, skills, integrations, security, and risks. That includes hardware or cloud, software and APIs, data flow, tooling, and the reality of your team’s expertise. See clear definitions and scope in the technical feasibility overviews from LaunchNotes and Chisel Labs:
- LaunchNotes on technical feasibility in product work: https://www.launchnotes.com/glossary/technical-feasibility-in-product-management-and-operations (opens new window)
- Chisel Labs on components and criteria: https://chisellabs.com/glossary/what-is-technical-feasibility/ (opens new window)
The TELOS lens is useful. Technical, Economic, Legal, Operational, and Scheduling, reviewed together, keep you honest. If the technical side is weak, the rest will crack.
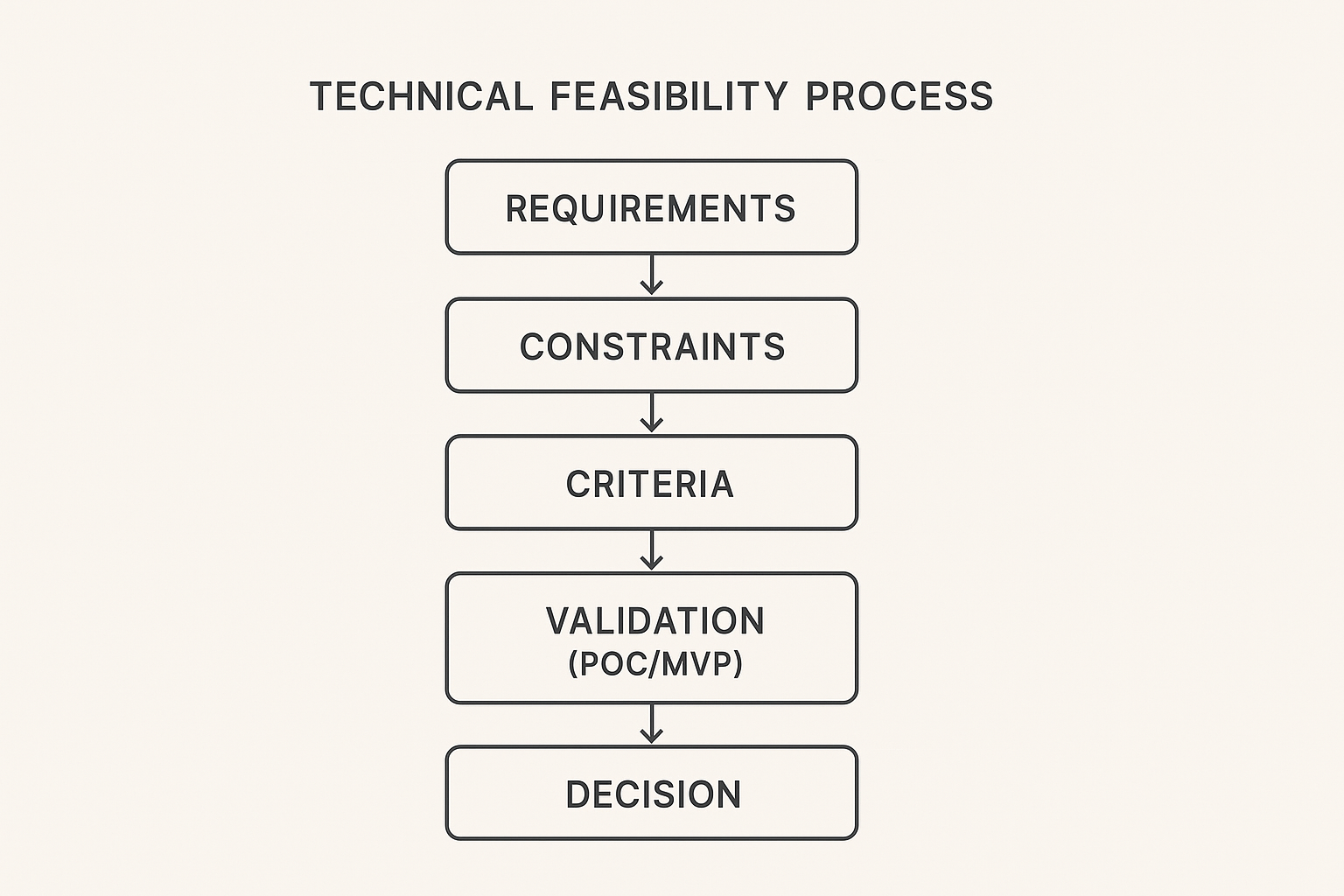
# A practical technical feasibility playbook
Use a repeatable process. Adjust depth by project size, but never skip steps.
- Define crisp requirements
- Separate functional from non functional. Spell out performance, scalability, uptime, security, and maintainability.
- Anchor numbers. Example: 500 requests per second per region, P95 latency under 200 ms, 99.9 percent availability.
- List constraints and assumptions
- Timebox, budget, mandated tech, compliance, vendor contracts, legacy systems.
- Document assumptions so you can test and retire them as facts arrive.
- Set evaluation criteria
- Benchmarks for performance, scalability headroom, integration complexity, risk profile, and operational burden.
- Decide pass or fail thresholds before you test.
- Research precedent and patterns
- Look for similar systems and known failure modes. Favor proven integration patterns over novelty when risk is high.
- Validate what is uncertain
- Use proofs of concept, spikes, or an MVP to de risk the hardest parts.
- Decide with evidence
- Accept outcomes. Adjust scope, add time, or cancel if findings do not meet your thresholds.
Tip: move quality topics to the front. Security, privacy, and reliability choices reshape architecture, not just polish it later.
# PoC, MVP, and spikes for feasibility
When should each tool be used, and why?
- Proof of concept: answers can it be built. Pick one or two critical unknowns and run a small, time boxed experiment with explicit success criteria. Good framing on validation stages: https://www.coherentsolutions.com/insights/proof-of-concept-prototype-and-mvp-product-validation-stages-explained (opens new window)
- MVP prototype: answers can users use it at acceptable performance. Build the narrowest slice that exercises integration, load, and operability end to end.
- Technical spike: answers a sharp question fast. Example: will the existing auth service support device flow without breaking SSO? One sprint, then decide.
Keep scope surgical. A PoC is not a shadow product. Define clear cutoffs like peak throughput met within 10 percent CPU headroom, or integration handshake completed with retries under 3 seconds.
# Architecture and integration checks
Feasibility weakens at the seams. Spend extra time where systems meet.
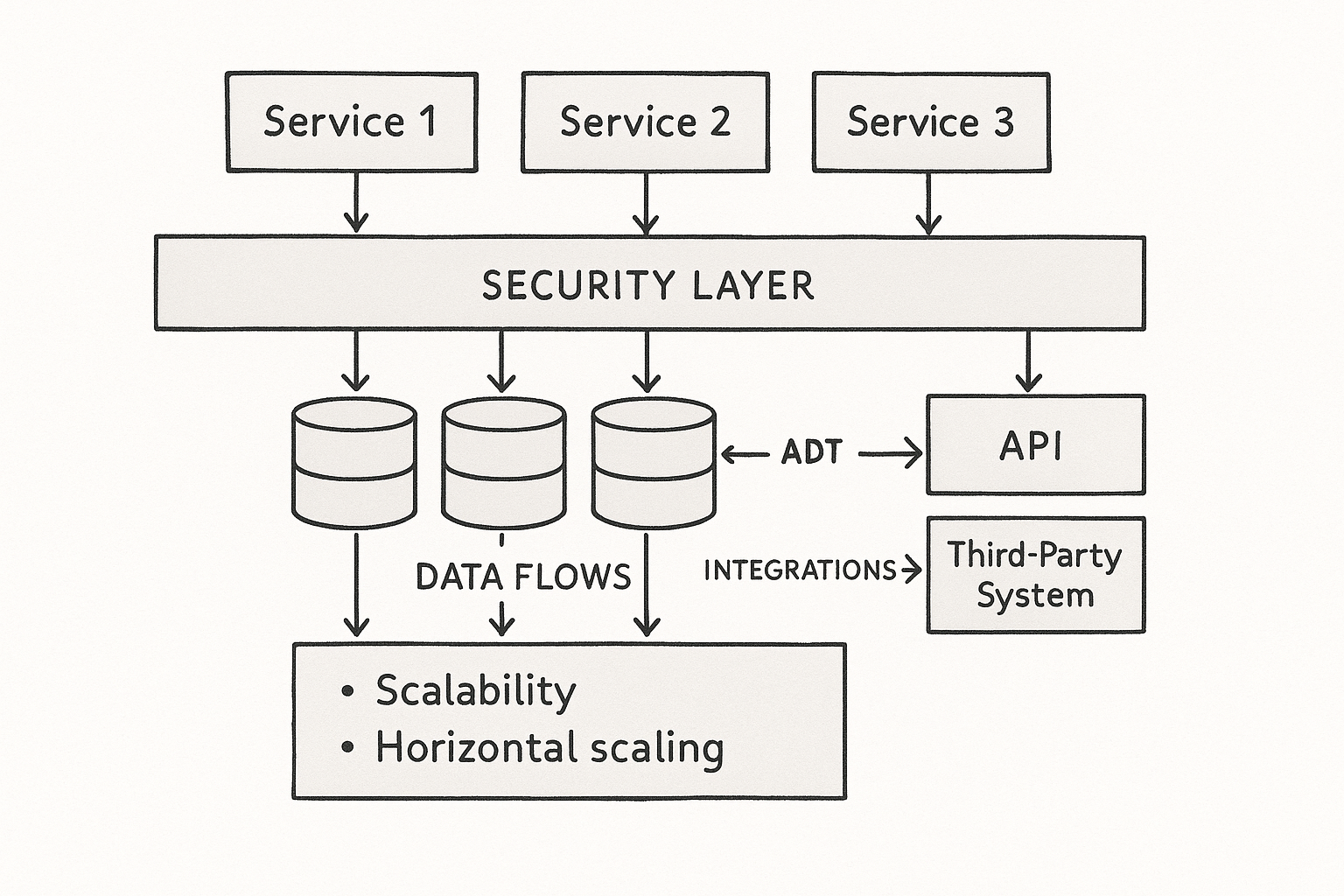
Run a targeted architecture review:
- Data paths: volumes, fan out, backpressure, failure handling.
- Integrations: versioning strategy, idempotency, rate limits, retries, fallbacks.
- Security and compliance: secrets, encryption, audit trails, data residency.
- Operability: logs, metrics, traces, SLOs, on call runbooks.
- Scalability: horizontal vs vertical limits, warmup behavior, cache strategy.
If an integration or compliance control is mandatory, test it early. Do not assume your vendor SDK covers your edge cases.
# Common pitfalls that break feasibility
Many failures are pattern repeats. Name them, then avoid them.
- Biased assessments: builders grading their own homework. Independent eyes reduce optimism bias. Practical guidance on avoiding skewed studies: https://groundfloorpartners.com/blog/common-feasibility-study-mistakes-and-how-to-avoid-them/ (opens new window)
- Vague scope: fuzzy inputs produce fuzzy answers. Replace goals like faster checkout with measurable targets like P95 under 300 ms across three payment gateways.
- Rushing the study: time saved now becomes schedule slips later. Depth scales with complexity.
- Narrow teams: only backend or only infra. Bring architects, security, data, and operations to the table.
- Cherry picking findings: ignoring red flags does not reduce risk. Escalate and revisit scope or timelines.
# Feasibility inside real project constraints
The iron triangle is real. Scope, cost, and time move together. Technical feasibility must sit inside those bounds and account for resources, quality, and risk.
- Resources: the best design fails if you cannot staff it. If you need a cloud network specialist you do not have, feasibility is at risk until that gap is closed.
- Quality: 99.99 percent uptime implies active active regions, health checks, and failover drills. If the budget cannot carry that, reset the target or change the plan.
- Risk: a theoretically possible approach that depends on immature tech may be infeasible for your risk tolerance.
For a simple primer on aligning feasibility and schedule, see Asana’s feasibility study overview: https://asana.com/resources/feasibility-study (opens new window)
# Quick answers to common questions
- What is a technical feasibility study? A structured evaluation of whether you can deliver the required functionality and quality within your constraints using your technology, people, and processes. A clear definition with elements here: https://chisellabs.com/glossary/what-is-technical-feasibility/ (opens new window)
- When should I run it? During initiation and again at major milestones. Treat it as living, not a one and done report.
- How deep should I go? Match depth to risk. New tech, heavy compliance, or many integrations call for PoCs and spikes.
- PoC or MVP? PoC proves the hardest technical assumption. MVP proves the whole slice works at acceptable user performance.
- How do I avoid bias? Separate the assessment team from sponsors, pre commit criteria, and publish assumptions.
# A small story from the trenches
On a recent migration, our team nearly committed to a streaming pipeline that looked elegant on paper. A two week spike showed subtle ordering and backfill issues under regional failovers. We swapped in a more boring pattern with stronger idempotency. That detour saved months of rework. Lesson: proving small details early is cheaper than heroic fixes later.
# Bring customer signal into feasibility
Technical choices are better when anchored in real demand. Before you scale, confirm that what you plan to build matters to users and stakeholders. We use structured feedback to shape scope and reduce waste. If you want a lightweight way to capture and prioritize input alongside your roadmap, review the tools on our features page: https://sleekplan.com/features/ (opens new window)
# Case patterns worth remembering
- Success with realism: complex transit systems that invested in deep feasibility up front, including integration and geotechnical risks, kept delivery credible and phased. Clarity beat optimism.
- Failure through optimism: projects that ignored cost, schedule, or integration warnings burned millions without shipping a usable system. Panorama Consulting’s public sector write ups show how known risks, left unresolved, cascade into organizational failure: https://www.panorama-consulting.com/information-technology-project-failure/ (opens new window)
# Implementation checklist
Use this as a pragmatic guardrail for your next feasibility cycle.
- Scope is measurable and documented.
- Constraints and assumptions are written and owned.
- Evaluation criteria and pass or fail thresholds are agreed.
- Precedent research and architecture review complete.
- PoC or spike covers the riskiest assumptions with clear success metrics.
- Security, privacy, and compliance mapped to controls and tests.
- Resource plan staffed with real names and backfills.
- Schedule reflects validation and hardening time, not only build time.
- Decision log closed with rationale and next steps.
# Closing thought
Good feasibility work is quiet, almost invisible. You spot weak joints early, you trim scope with intent, and you choose sturdy patterns over flashy ones. The result is simple. Fewer surprises, fewer escalations, and a product that holds up in production.